Address key industrial Internet of Things (IIoT) challenges
Uday Mudoi, Microsemi Corporation According to the latest report from BI Intelligence, by 2020, the Internet of Things (IoT) will connect 34 billion devices. Among these connections, commercial and government connections account for more than 55%. As IoT is expected to improve efficiency (such as lower operating costs and increase productivity), embedded machine-to-machine (M2M) communications in “smart objects†will become increasingly popular in commercial, industrial, and government entities. Unlike consumer IoT, the failure of industrial IoT (IIoT) can cause catastrophic and even fatal consequences. Therefore, the requirements for data integrity, reliability, and security are much more stringent. The threat of collapse poses a huge security risk to the entire digital network. However, the unprecedented transparency and efficiency prospects of IIoT are still very attractive. To achieve real-time visibility and control in connecting IIoT objects requires a high-performance, low-latency network with remote management capabilities. Ethernet has advantages including standardization, versatility, high performance, and low cost, and it has been the network technology choice for enterprises, data centers, and many service providers. However, most existing IIoT networks use private network protocols and have a variety of legacy equipment, which complicates the modernization of all IP Ethernet infrastructures. These heterogeneous network upgrade strategies, in migrating to the standard low-cost network solutions provided by Ethernet, must balance the necessary system reliability, certainty, and security of the industrial setup. In this article, we will discuss the three major challenges faced by IIoT system designers at the system level – security, determinism, and network mobility – and leverage Ethernet-to-Ethernet switching solutions, programmable devices, high-precision timing, and Ethernet. The technology portfolio of power supply and application optimization software provides tips and strategies for addressing these challenges. Today, the premise of industrial network security is to use firewalls to isolate corporate networks and isolate them from the Internet. The broader approach of securing industrial networks often results in network downtime or expensive network topology changes, or even a combination of the two, which can hurt device productivity and company revenue, and sometimes even compromise security. However, for a given network, it is wrong to believe that it is protected simply because it is isolated from the Internet. As the latest cyber attacks show, isolating modern industrial networks from the Internet actually makes them even less secure, because in this way, industrial networks are more difficult to manage and diagnose problems. As companies evolve their supply chains, adopt new technologies, or respond to new competitive threats and opportunities, isolated networks are difficult to expand and reconfigure. IIoT network security must adopt multiple layers of methods to protect the data plane, management (network and components), and control (protocol) planes. All three need protection, especially for M2M communications. The typical approach is to rely on data encryption, manage and control traffic, perform authentication, authorization and accounting (AAA), and data integrity. Network encryption is another layer that ensures the security of all network traffic. In Ethernet, MACsec (IEEE 802.1AE) and Keysec (now part of IEEE 802.1X) are L2 encryption and key management protocols to ensure the security of Ethernet physical ports and VLANs. The IEEE 802.1AEbn now includes strong 256-bit encryption required by certain government agencies, further enhancing confidentiality. Although relying solely on encryption does not guarantee network security, networked devices and endpoints use powerful 256-bit encryption (such as MACsec) to provide the authentication, data integrity, and user confidentiality required for an Ethernet-based IIoT network. . In addition, using an FPGA with built-in security capabilities, a root of trust can be provided in the system. Typically, these devices are used to securely boot an external processor and add another layer of security to prevent tampering with network elements looking for keys. As IIoT applications become more widespread, companies will increasingly rely on acquiring data at the edge of the network, leveraging large-scale data analytics and cloud computing to expand the processing and practical use of all of this data. Internet connection is a must. The Central Security orchestration approach works closely with the Internet and distributed networking hardware to provide effective ways to secure the IIoT network. Finally, for an industrial network, to ensure network reliability and uptime without restricting operations, it is necessary to adopt a multi-layer security approach. When considering the deterministic performance and network reliability of Ethernet, one expects specific functions to occur within a precise time frame. This is possible when each network element is time-aware and able to recognize if it is transmitting Ethernet packets "on time." However, this is only part of the solution. Today, there is already a mechanism to synchronize and allocate precise "times" within the Ethernet using IEEE 1588v2. However, the latest time-sensitive network (TSN) standard brings time-oriented methods of traffic scheduling to system developers. The TSN standard was developed by the IEEE 802 Working Group to broaden the capabilities of Ethernet to make it a true industrial-grade real-time communications protocol. Its components include clock synchronization, time-based message processing, frame preemption, and seamless redundancy. TSN (AVB Gen2) is a set of standards that provides the following features: • Timing and synchronization of time-sensitive applications (IEEE 802.1ASbt) • Scheduled Traffic Enhancement (IEEE 802.1Qbv) • Frame Preemption (IEEE 802.1Qbu) • Redundant network path control and reservation (IEEE 802.1Qca) • Enhanced Stream Reservation Protocol (SRP) support for Qbu/Qbv/Qca/CB (IEEE 802.1Qcc) • Seamless redundancy (IEEE 802.1CB) In addition to improving usability and performance, for example, IEEE 802.1ASbt adds a one-step timestamp support that reduces the number of packets required to convey network timing information compared to the two-step approach used by previous generation standards. The reduction of packet traffic and computing power benefits a wide range of daisy-chain time perception networks. IEEE 802.1ASbt also enhances the availability of timing information by providing multiple levels of synchronization to obtain accurate timing at each network node. The new TSN feature will give real-time determinism and low latency for Ethernet IIoT application communications. This should eliminate the last barriers that may hinder the adoption of Ethernet as the backbone of the IIoT network, driving the convergence of critical and non-critical controls and data traffic in a single network. Although TSN Ethernet may eventually become the deterministic backbone for industrial network deployment, proprietary interfaces will still exist for the foreseeable future. FPGA/SoCs that can switch between Ethernet, IEEE 1588, TSN, and proprietary industrial protocols while maintaining deterministic behavior will be critical. Compared with MCUs, determinism is one of the key advantages of FPGAs. For example, networked motor control applications using EtherCAT will benefit from the deterministic nature of the FPGA fabric. The FPGA can perform protocol conversion and motor control algorithms, all with the lowest possible latency. Compared to MCUs, FPGAs can synchronize with remote nodes, transmit data in deterministic ways and perform deterministic motor control. The IIoT network will eventually migrate to IP/Ethernet, but it is important to identify the two main factors that are unique to this transformation: • Ethernet standards, components, and systems designed for local area networks (LANs) are not naturally suitable for IIoT networks. • The IIoT migration requires a balancing act to support existing “non-standard†agreements and prepare the network for initial innovation. Therefore, when faced with a typical industrial network consisting of heterogeneously installed base stations of legacy equipment using several proprietary network protocols, the key elements that designers should look for in order to simplify the migration of their networks to Ethernet are: • Ethernet multiprotocol support and fieldbus interfaces to ensure interoperability and scalability of large heterogeneous networks • Optimized Ethernet switch software stack for easy deployment and management • Unified hardware and software for reliable real-time determinism and low latency required for industrial communications • Port configuration flexibility and synchronization options while meeting IIoT environmental and operational requirements • Up to 95W of Power over Ethernet (PoE) to safely power remote devices, simplifying deployment Using the practical combination of the following hardware and software, it is possible to implement all of the above items: • Secure Low-Power FPGA Solutions • Optimized Ethernet Switching Silicon for Industrial Deployment • Not only provides management and monitoring capabilities, but also has a software stack for the security orchestration software ecosystem • Ruggedized PoE Solution Designed for Industrial Settings Everyone must understand that there is no "universal universal strategy" for the IIoT system. Options that support PoE, synchronization requirements, and data encryption can help provide a seamless upgrade of the underlying hardware and software solutions. The computational needs of other situations may be able to be implemented using integrated CPUs or FPGAs or stand-alone CPUs in the switch. The IIoT application design requires a perceptual migration path and adopts new technologies for implementing deterministic networks, while recognizing that in a system environment where industrial networks exist, the maximum network uptime is more important than the latest network upgrades. In a world where network breakdowns cannot occur, industry must cross over old technologies, protocols, and first-generation industrial Ethernet networks.
Semiconductor Stud Devices are mainly used for rectifying and switching
By using the unidirectional conductivity of the diode, alternating direction alternating current can be transformed into pulse direct current in a single direction.
Applications for Medium power switching and DC power supplies.
Semiconductor Stud Devices,Stud Mounted Semiconductor Devices,Stud Mounted Power Semiconductor Device,Ir Semiconductor Stud Thyristor YANGZHOU POSITIONING TECH CO., LTD. , https://www.cnchipmicro.com
safety 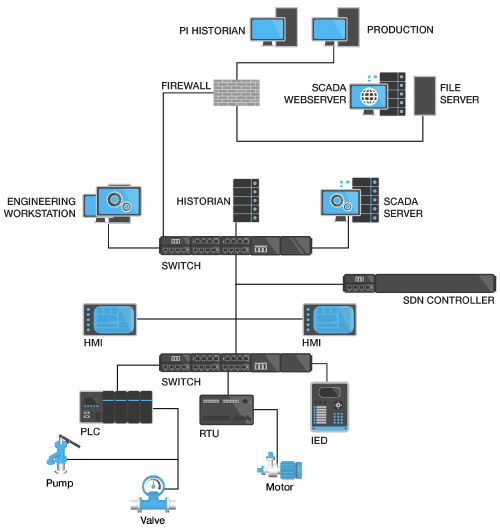
Figure 1 Industrial automation network. As the network becomes more flexible, the security architecture continues to evolve.
Certainty
Network migration
in conclusion